Troubleshooting Computer Accounts
Active Directory domains treat computers as security principals. This means that a computer, just like a user, has an account—or, more specifically, properties within the computer object such as a name, a password, and a SID. Like user accounts, computer accounts require maintenance and, occasionally, troubleshooting. This topic focuses on skills and concepts related to troubleshooting computer objects.
Deleting and Disabling and Resetting Computer Accounts
Computer accounts, like user accounts, maintain a unique SID, which enables an administrator to grant permissions to computers. Also like user accounts, computers can belong to groups. Therefore, like user accounts, it is important to understand the effect of deleting a computer account. When a computer account is deleted, its group memberships and SID are lost. If the deletion is accidental, and another computer account is created with the same name, it is nonetheless a new account, with a new SID. Group memberships must be reestablished, and any permissions assigned to the deleted computer must be reassigned to the new account. Delete computer objects only when you are certain that you no longer require those security-related attributes of the object.
To delete a computer account using Active Directory Users And Computers, locate and select the computer object and, from the Action menu or the shortcut menu, select the Delete command. You will be prompted to confirm the deletion and, because deletion is not reversible, the default response to the prompt is No. Select Yes and the object is deleted.
The DSRM command-line tool introduced in earlier topic allows you to delete a computer object from the command prompt. To delete a computer with DSRM, type:
DSRM ObjectDN
Where ObjectDN is the distinguished name of the computer, such as “CN=Desktop15, OU=Desktops,DC=mcseweb,DC=local.” Again, you will be prompted to confirm the deletion.
If a computer is taken offline or is not to be used for an extended period of time, you may disable the account. Such an action reflects the security principle, that an identity store allow authentication only of the minimum number of accounts required to achieve the goals of an organization. Disabling the account does not modify the computer’s SID or group membership, so when the computer is brought back online, the account can be enabled.
The context menu, or Action menu, of a selected computer object exposes the Disable Account command. A disabled account appears with a red “X” icon in the Active Directory Users And Computers snap-in, as shown in below Figure.
While an account is disabled, the computer cannot create a secure channel with the domain. The result is that users who have not previously logged on to the computer, and who therefore do not have cached credentials on the computer, will be unable to log on until the secure channel is reestablished by enabling the account.
To enable a computer account, simply select the computer and choose the Enable Account command from the Action or shortcut menus.
To disable or enable a computer from the command prompt, use the DSMOD command. The DSMOD command modifies Active Directory objects. The syntax used to disable or enable computers is:
DSMOD COMPUTER ComputerDN -DISABLED YES
DSMOD COMPUTER ComputerDN -DISABLED NO
If a computer account’s group memberships and SID, and the permissions assigned to that SID, are important to the operations of a domain, you do not want to delete that account. So what would you do if a computer was replaced with a new system, with upgraded hardware? Such is one scenario in which you would reset a computer account.
Resetting a computer account resets its password, but maintains all of the computer object’s properties. With a reset password, the account becomes in effect “available” for use. Any computer can then join the domain using that account, including the upgraded system.
In fact, the computer that had previously joined the domain with that account can use the reset account by simply rejoining the domain.
The Reset Account command is available in the Action and context menus when a computer object is selected. The DSMOD command can also be used to reset a computer account, with the following syntax:
dsmod computer ComputerDN -reset
The NETDOM command, included with the Windows Server 2003 Support Tools in the CD-ROM’s Support\Tools directory, also enables you to reset a computer account.
Recognizing Computer Account Problems
Computer accounts, and the secure relationships between computers and their domain are robust. In the rare circumstance that an account or secure channel breaks down, the symptoms of failure are generally obvious. The most common signs of computer account problems are:
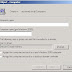
Messages at logon indicate that a domain controller cannot be contacted; that the computer account may be missing; or that the trust (another way of saying “the secure relationship”) between the computer and the domain has been lost. An example is shown in below Figure.
* Error messages or events in the event log indicating similar problems or suggesting that passwords, trusts, secure channels, or relationships with the domain or a domain controller have failed.
* A computer account is missing in Active Directory.
If one of these situations occurs, you must troubleshoot the account. You learned earlier how to delete, disable, and reset a computer account and, at the beginning of the chapter, how to join a machine to the domain.
The rules that govern troubleshooting a computer account are:
A. If the computer account exists in Active Directory, it must be reset.
B. If the computer account is missing in Active Directory, you must create a computer account.
C. If the computer still belongs to the domain, it must be removed from the domain by changing its membership to a workgroup. The name of the work-group is irrelevant. Best practice is to try and choose a workgroup name that you know is not in use.
D. Rejoin the computer to the domain. Alternatively, join another computer to the domain; but the new computer must have the same name as the computer account.
To troubleshoot any computer account problem, apply all four rules. These rules can be addressed in any order, except that Rule D, involving rejoining the computer to the domain, must as always be performed as the final step. Let’s examine two scenarios.
In the first scenario, a user complains that when he or she attempts to log on, the system presents error messages indicating that the computer account might be missing. Applying Rule A, you open Active Directory Users And Computers and find that the computer account exists. You reset the account. Rule B does not apply—the account does exist. Then, using Rule C, you disjoin the system from the domain and, following Rule D, rejoin the domain.
In a second scenario, if a computer account is reset by accident, the first item that has occurred is Rule A. Although the reset is accidental, you must continue to recover by applying the remaining three rules. Rule B does not apply because the account exists in the domain. Rule C indicates that if the computer is still joined to the domain, it must be removed from the domain. Then, by Rule D, it can rejoin the domain.
With these four rules, you can make an informed decision, on the job or on the certification exams, about how to address any scenario in which a computer account has lost functionality.
Monday, January 18, 2010
Subscribe to:
Post Comments (Atom)







No comments:
Post a Comment